5.2. Describe the important and distinguishing properties of Peer to Peer computing and the Grid. How is this peer to peer and the Grid architecture changing work flow and service-oriented applications?
Peer to Peer computing is important for distributed computing, data/content sharing, communication and collaboration, or platform services.
HP(2003) states that the term “peer-to-peer” refers to a class of systems and applications that employ distributed resources to perform a function in a decentralized manner. The resources encompass computing power, data (storage and content), network bandwidth, and presence (computers, human, and other resources). The critical function can be distributed computing, data/content sharing, communication and collaboration, or platform services.
Furthermore, peer-to-peer(P2P) enables valuable externalities, by aggregating resources through low-cost interoperability, the whole is made greater than the sum of its parts escalator, it also lowers cost of ownership and cost sharing, by using existing infrastructure and by eliminating or distributing the maintenance cost, moreover, it enables anonymity/privacy, by incorporating these requirements in the design and algorithms of P2P systems and applications, and by allowing peers a greater degree of autonomous control over their data and resources
Grid computong is important for support various business processes.
HP(2009) states resources can be dynamically provisioned to users or applications that need them in grid computing. Resources can be shared within a workgroup, department or enterprise; among different organizations and geographies; and even with groups outside the enterprise in collaborative projects. Grids can be designed to support various business processes. Grid technologies use emerging Web services standards such as XML, SOAP and WSDL and have long been used for scientific and technical work, where dispersed computers are linked to create virtual supercomputers that rapidly process vast amounts of information.
Domenico Talia (2003) states that Grid and P2P can be distinguished by the following points:
First, Security is a central theme in grids, and several efforts are devoted to integrating relevant mechanisms for authentication, authorization, integrity, and confidentiality in grid platforms. In contrast, P2P systems originate in "open communities," in which users share more generic goals such as retrieving music from the Internet, rather than specific objectives such as participating in high-energy physics simulations.
Second, Connectivity, Grids generally include powerful machines that are statically connected through high-performance networks with high levels of availability. On the other hand, the number of accessible nodes is generally low because access to grid resources is bonded to rigorous accounting mechanisms. Conversely, P2P systems are composed mainly of common desktop computers that are connected intermittently to the network, remaining available for a limited time with reduced reliability. The number of nodes connected in a P2P network at a given time is much greater than in a grid. Thus, the grid connectivity approach is still too stiff for new nodes and user access and accounting; it could benefit from the more flexible connectivity models used in P2P networks today.
Third, Fault Tolerance, the dynamic nature of grids necessitates some level of fault tolerance—especially for highly distributed code, such as parameter-sweep applications, which can fork numerous similar, independent jobs on many nodes.
Beyond simple checkpointing and restarting, reliability and fault tolerance are largely unexplored in grid models and tools. The Globus information system allows fault detection, for instance, but developers must implement fault tolerance at the application level. For greater reliability, designers of fault-tolerance mechanisms and policies for grids should consider using decentralized P2P algorithms, which avoid centralized services that can represent critical failure points.
Peer to peer is changing the work flow and service-oriented applications, firstly i want to describe how is traditional work flow and service-oriented application, please see the below figure:

The traditional work flow and service-oriented application are one-to-many, that's one server serves many clients, for example, one FTP server can allow many ftp client to download / upload online files.
Conversely, P2P's work flow and service-oriented application are many-to-many, please refer to the below figure, you can find that all nodes are multi-connected between each others, this design allows for scalable incremental growth and aggregates tremendous amount of computation and storage resources, for example, internet users cooperate to share such as music files
Napster, Gnutella, Morpheus and KaZaA; online communication application such as Skype and free Internet IP telephony.

And Grid architecture is changing the work flow and service-oriented applications, it is because...
a.) need for people-services as well as middleware services(computer services), for example, credential authorities, VO managers, support.
b.) Single sign-on to resources in multiple organisations.
c.) Flexible collaboration across multiple administrative domains for example sharing data, computers, instruments, application software
d.) It is a virtual organisation covered people and resources collaborating for example across admin and organisational boundaries.
References:
HP(2003). “Peer to Peer Computing”. Received 20th March, 2009 from URL - http://www.hpl.hp.com/techreports/2002/HPL-2002-57R1.pdf
HP(2009). “What is grid computing?”. Received 20th March, 2009 from URL - http://h71028.www7.hp.com/enterprise/cache/125371-0-0-0-121.html
Domenico Talia (2003), Paolo Trunfio, "Toward a Synergy Between P2P and Grids," IEEE Internet Computing, vol. 7, no. 4, pp. 96, 94-95.














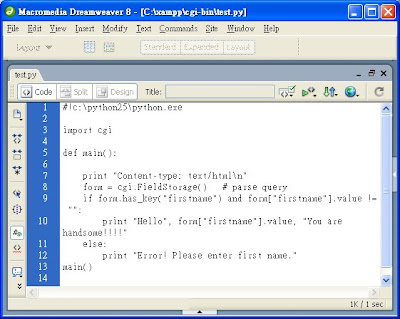














 b.) Input something in the textbox and click button named "Enter information".
b.) Input something in the textbox and click button named "Enter information". 8.4. The corresponding PHP file is add_record.php used with the POST method:
8.4. The corresponding PHP file is add_record.php used with the POST method:





 The below screendump shows some php code which is replaced by $SERVER_NAME.
The below screendump shows some php code which is replaced by $SERVER_NAME.





